以前的老文章,今天有空,也一并转过来吧!
样本见附件!
用PEid查壳显示为:Microsoft Visual C++ 6.0
但是用OD载入后,有提示: 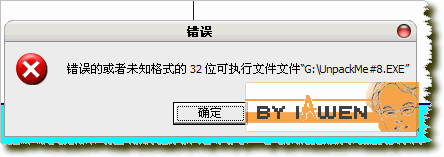
确定后,OD停在:
0103B070 > 55 push ebp
0103B071 8BEC mov ebp,esp
0103B073 6A FF push -1
0103B075 68 FC424000 push 4042FC
0103B07A 68 04214000 push 402104
0103B07F 64:A1 00000000 mov eax,dword ptr fs:[0]
0103B085 50 push eax
0103B086 64:8925 00000000 mov dword ptr fs:[0],esp
0103B08D 83EC 58 sub esp,58
0103B090 53 push ebx
0103B091 56 push esi
0103B092 57 push edi
0103B093 8965 E8 mov dword ptr ss:[ebp-18],esp
0103B096 FF15 A0B00301 call dword ptr ds:[103B0A0] ; UnpackMe.0103B0A4
Ctrl+G来到:VirtualAlloc,在段尾下断:
7C809A64 E8 09000000 call kernel32.VirtualAllocEx
7C809A69 5D pop ebp
7C809A6A C2 1000 retn 10===========在此F2下断
F9运行,在7次中断后,取消断点,F7进入后来到:
01015F2A A3 F8850201 mov dword ptr ds:[10285F8],eax
01015F2F 8B15 F4850201 mov edx,dword ptr ds:[10285F4]
01015F35 C702 0D661900 mov dword ptr ds:[edx],19660D
01015F3B A1 F8850201 mov eax,dword ptr ds:[10285F8]
01015F40 C700 5FF36E3C mov dword ptr ds:[eax],3C6EF35F
01015F46 C745 EC 00000000 mov dword ptr ss:[ebp-14],0
01015F4D C745 FC 00000000 mov dword ptr ss:[ebp-4],0
01015F54 68 00002E00 push 2E0000
01015F59 E8 40FCFFFF call UnpackMe.01015B9E
再次Ctrl+G来到:LoadLibraryA,在段尾下断:
7C801D9C FF75 08 push dword ptr ss:[ebp+8]
7C801D9F E8 ABFFFFFF call kernel32.LoadLibraryExA
7C801DA4 5E pop esi
7C801DA5 5B pop ebx
7C801DA6 5D pop ebp
7C801DA7 C2 0400 retn 4======================在此F2下断
中断后,取消断点返回到:
0102159E 8945 F0 mov dword ptr ss:[ebp-10],eax
010215A1 837D F0 00 cmp dword ptr ss:[ebp-10],0
010215A5 75 16 jnz short UnpackMe.010215BD
继续找段尾下断:
010216CC 68 64760201 push UnpackMe.01027664 ; ASCII "WriteFile"
010216D1 FF75 FC push dword ptr ss:[ebp-4]
010216D4 FF75 F8 push dword ptr ss:[ebp-8]
010216D7 E8 90FCFFFF call UnpackMe.0102136C
010216DC 83C4 0C add esp,0C
010216DF 8945 E0 mov dword ptr ss:[ebp-20],eax
010216E2 837D E0 00 cmp dword ptr ss:[ebp-20],0
010216E6 74 08 je short UnpackMe.010216F0
010216E8 8B45 E0 mov eax,dword ptr ss:[ebp-20]
010216EB A3 3C870201 mov dword ptr ds:[102873C],eax
010216F0 C9 leave
010216F1 C3 retn===============在此F2下断
F9运行中断后,取消断点,F7进入:
01021552 83C4 0C add esp,0C
01021555 68 F0550201 push UnpackMe.010255F0 ; ASCII "oleaut32.dll"
0102155A 6A 02 push 2
0102155C 68 A8830201 push UnpackMe.010283A8
01021561 E8 13000000 call UnpackMe.01021579
01021566 83C4 0C add esp,0C
01021569 68 AC550201 push UnpackMe.010255AC ; ASCII "kernel32.dll"
0102156E FF15 98860201 call dword ptr ds:[1028698] ; kernel32.GetModuleHandleA
01021574 8945 FC mov dword ptr ss:[ebp-4],eax
01021577 C9 leave
01021578 C3 retn=============在此继续F2下断
F9运行中断后,取消断点,F7进入:
0101C797 E8 EA7BFFFF call UnpackMe.01014386
0101C79C A1 04860201 mov eax,dword ptr ds:[1028604]
0101C7A1 8B48 04 mov ecx,dword ptr ds:[eax+4]
0101C7A4 894D EC mov dword ptr ss:[ebp-14],ecx
找段尾:
0101C923 /74 0E je short UnpackMe.0101C933
0101C925 |68 047C0201 push UnpackMe.01027C04 ; ASCII "oleaout32.dll"
0101C92A |8B55 F4 mov edx,dword ptr ss:[ebp-C]
0101C92D |52 push edx
0101C92E |E8 FD010000 call UnpackMe.0101CB30
0101C933 \8BE5 mov esp,ebp
0101C935 5D pop ebp
0101C936 C3 retn=============在此继续F2下断
F9运行中断后,取消断点,F7进入:
010162CB 8B4D EC mov ecx,dword ptr ss:[ebp-14] ; UnpackMe.0100739D
010162CE 894D 08 mov dword ptr ss:[ebp+8],ecx
010162D1 833D B4C90201 00 cmp dword ptr ds:[102C9B4],0
010162D8 74 13 je short UnpackMe.010162ED
010162DA 6A 00 push 0
010162DC 6A 00 push 0
010162DE 6A 00 push 0
010162E0 8B15 B4C90201 mov edx,dword ptr ds:[102C9B4]
010162E6 52 push edx
010162E7 FF15 B8870201 call dword ptr ds:[10287B8] ; user32.PostMessageA
010162ED 33C0 xor eax,eax
010162EF 5F pop edi
010162F0 5E pop esi
010162F1 5B pop ebx
010162F2 8BE5 mov esp,ebp
010162F4 5D pop ebp
010162F5 C3 retn=============在此继续F2下断
F9运行中断后,取消断点,F7进入:
0101572B 58 pop eax ; UnpackMe.0100739D
0101572C 894424 24 mov dword ptr ss:[esp+24],eax
01015730 61 popad
01015731 58 pop eax
01015732 58 pop eax
01015733 FFD0 call eax==========这里F7进入就直奔OEP了
01015735 E8 B8BF0000 call UnpackMe.010216F2
0101573A CC int3
0101573B CC int3
0101573C CC int3
0101573D CC int3
0101573E CC int3
0101573F CC int3
F7进入后:
------------------------------------------------------------------
0100739D 6A 70 push 70
0100739F 68 98180001 push UnpackMe.01001898
010073A4 E8 BF010000 call UnpackMe.01007568
010073A9 33DB xor ebx,ebx
010073AB 53 push ebx
010073AC 8B3D CC100001 mov edi,dword ptr ds:[10010CC] ; UnpackMe.01022254
010073B2 FFD7 call edi
010073B4 66:8138 4D5A cmp word ptr ds:[eax],5A4D
010073B9 75 1F jnz short UnpackMe.010073DA
先不急着DUMP出来,我们用ImportREC修复一下看看IAT,如下图: 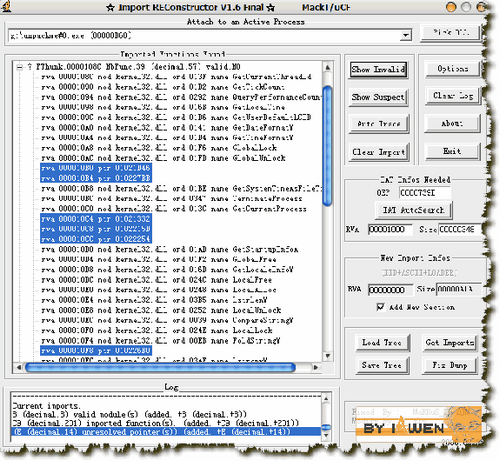
有许多无效的指针,等级一修复后,依然有几个,看来有IAT加密了,记录下几个无效的地址以及找到的OEP地址:
010010B0 01021D46 UnpackMe.01021D46
010010B4 010227BB UnpackMe.010227BB
OEP: 0100739D======739D
重新载入程序后,我们在010010B0上下“断点--硬件访问断点--DWORD”,如下图: 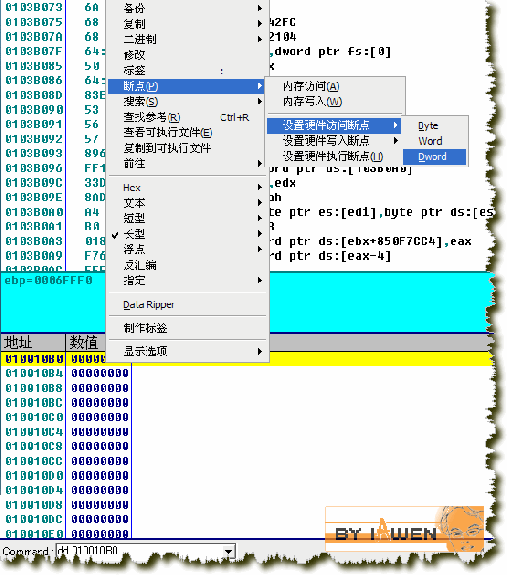
同时记得在VirtualAlloc的段尾下断,F9运行,直到数据窗口出现:
010010B0 7C810C6D kernel32.GetFileInformationByHandle,呵呵,这就是我们需要的了
此时代码停在:
0101C6A6 /EB 2C jmp short UnpackMe.0101C6D4======停在此处
0101C6A8 |8B55 F4 mov edx,dword ptr ss:[ebp-C]
0101C6AB |8B02 mov eax,dword ptr ds:[edx]
0101C6AD |25 FFFF0000 and eax,0FFFF
0101C6B2 |8945 D0 mov dword ptr ss:[ebp-30],eax
0101C6B5 |8B4D D0 mov ecx,dword ptr ss:[ebp-30]
0101C6B8 |51 push ecx
0101C6B9 |8B55 EC mov edx,dword ptr ss:[ebp-14]
0101C6BC |52 push edx
0101C6BD |FF15 A8860201 call dword ptr ds:[10286A8]
0101C6C3 |8945 D4 mov dword ptr ss:[ebp-2C],eax
0101C6C6 |837D D4 00 cmp dword ptr ss:[ebp-2C],0
0101C6CA |74 08 je short UnpackMe.0101C6D4
0101C6CC |8B45 E0 mov eax,dword ptr ss:[ebp-20]
0101C6CF |8B4D D4 mov ecx,dword ptr ss:[ebp-2C]
0101C6D2 |8908 mov dword ptr ds:[eax],ecx
0101C6D4 \8B55 F0 mov edx,dword ptr ss:[ebp-10]
[c/ode]
我们F8单步,看看IAT是如何加密成:
010010B0 01021D46 UnpackMe.01021D46
[code]
0101C6E1 8B45 DC mov eax,dword ptr ss:[ebp-24]
0101C6E4 50 push eax
0101C6E5 8B0D C07B0201 mov ecx,dword ptr ds:[1027BC0] ; UnpackMe.01027BC4
0101C6EB 51 push ecx
0101C6EC 8B55 E0 mov edx,dword ptr ss:[ebp-20]
0101C6EF 52 push edx
0101C6F0 E8 9B070000 call UnpackMe.0101CE90========单步到此后,F7进入
0101C6F5 83C4 0C add esp,0C
0101C6F8 ^ E9 3EFFFFFF jmp UnpackMe.0101C63B
F7进入后:
0101CED2 8B45 08 mov eax,dword ptr ss:[ebp+8]
0101CED5 50 push eax
0101CED6 FF15 2C870201 call dword ptr ds:[102872C] ; kernel32.VirtualProtect
0101CEDC 85C0 test eax,eax
0101CEDE 75 0A jnz short UnpackMe.0101CEEA
0101CEE0 B9 0B0000EF mov ecx,EF00000B
0101CEE5 E8 482B0000 call UnpackMe.0101FA32
0101CEEA 8B4D 08 mov ecx,dword ptr ss:[ebp+8]
0101CEED 8B55 F8 mov edx,dword ptr ss:[ebp-8]
0101CEF0 8B02 mov eax,dword ptr ds:[edx]
0101CEF2 8901 mov dword ptr ds:[ecx],eax==========*****注意此时的提示窗口
0101CEF4 8D4D F4 lea ecx,dword ptr ss:[ebp-C]
0101CEF7 51 push ecx
0101CEF8 8B55 F0 mov edx,dword ptr ss:[ebp-10]
0101CEFB 52 push edx
0101CEFC 6A 04 push 4
0101CEFE 8B45 08 mov eax,dword ptr ss:[ebp+8]
0101CF01 50 push eax
0101CF02 FF15 2C870201 call dword ptr ds:[102872C] ; kernel32.VirtualProtect
0101CF08 C745 FC 01000000 mov dword ptr ss:[ebp-4],1
0101CF0F 8B45 FC mov eax,dword ptr ss:[ebp-4]
0101CF12 8BE5 mov esp,ebp
0101CF14 5D pop ebp
0101CF15 C3 retn
单步到此时:
0101CEF2 8901 mov dword ptr ds:[ecx],eax==========*****注意此时的提示窗口
//eax=01021D46 (UnpackMe.01021D46)
//ds:[010010B0]=7C810C6D (kernel32.GetFileInformationByHandle)
将正确的IAT地址用01021D46替换了,我们NOP掉,修改后如下图: 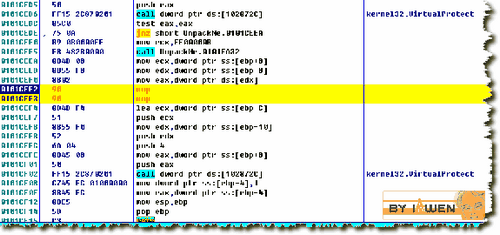
然后我们取消所有的断点,Ctrl+G来到OEP:0100739D,F2下断后,F9运行到OEP后,取消断点,再用ImportREC看一下: 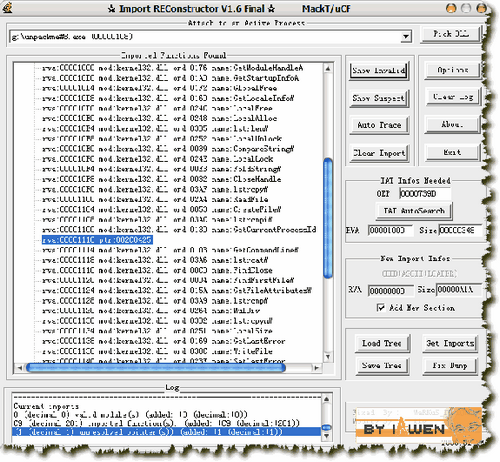
获取IAT表后,有一无效的指针,那就是:GetProcAddress
手工修复一下,DUMP出程序,然后修复、运行,OK!
——————————————————————————–
【版权声明】: 转载请注明作者并保持文章的完整, 谢谢!
2008年06月05日 10:00:07
